Skaffa nya IT-kunskaper, bli certifierad och lyft din IT-karriär till nya höjder utan att spränga banken!
Unlimited Training - IT kurser och certifieringar gjort enkla och otroligt billiga. Få tillgång till 60+ LIVE-kurser för mindre än priset för en kurs.











course: GIAC Security Essentials (GSEC)
Varighet: 5 days
Format: Virtual or Classroom
![]() Förbereder till Examen :
GIAC Security Essentials (GSEC)
Förbereder till Examen :
GIAC Security Essentials (GSEC)
![]() Förbereder till Certifiering :
GIAC Security Essentials (GSEC)
Förbereder till Certifiering :
GIAC Security Essentials (GSEC)
Löft dine cybersäkerhetsfærdigheder med kurset Security Essentials (GSEC). Ledet af certifierade brancheeksperter ger detta program omfattande träning i väsentliga säkerhetsprincipper. Mestre nyckelkoncept och praktiska färdigheter för att skydda digital aktivering. Bekräfta dina färdigheter med GSEC-certifiering, och positionera dig som en kompetent och efterspurgt professionell inom det stadigt utvecklade området av cybersäkerhet.
Utbildningskursen GIAC Security Essentials (GSEC) är utformad för individer som söker en omfattande förståelse för cybersäkerhetsprinciper och -praxis. Det är lämpligt för blivande cybersäkerhetsproffs, IT-personal och systemadministratörer. Kursen behandlar ämnen som säkerhetsprinciper och policyer, nätverkssäkerhet, säkerhetsbedömning och -revision, säkerhetskontroller och -tekniker, incidentrespons och hantering samt kryptografi. Genom att slutföra kursen och erhålla GSEC-certifieringen, visar individer sin färdighet i grundläggande cybersäkerhetskoncept och får kunskap om att säkra nätverk, bedöma sårbarheter, implementera säkerhetskontroller och svara på säkerhetsincidenter. Certifieringen validerar deras expertis inom viktiga säkerhetsområden och ökar deras trovärdighet inom cybersäkerhetsområdet.

Readynez är den bästa utbildningsleverantören jag har använt på många år. Deras kundservice är förstklassig, priserna är mycket konkurrenskraftiga och instruktörerna är excellent.

Lätt att delta över Teams och en utmärkt instruktör gav mig stort värde för den tid jag investerade.
Ditt personliga Learning Program ger dig de färdigheter du behöver så att du kan göra mer av det du älskar. Learning Programmet's tre steg är utformade så att du lär dig nya färdigheter som kommer att öppna upp nya möjligheter för dig.
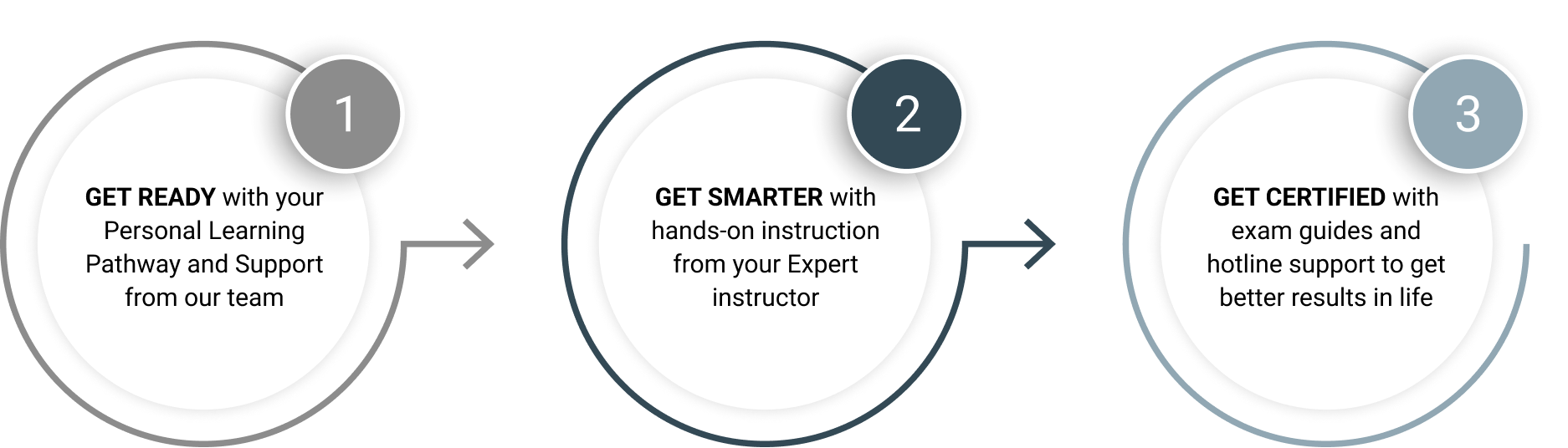
Readynez365 plattformen erbjuder en digital väg för alla dina inlärningsresurser, från förberedelser till examen, vilket gör det till en smidig väg till nya tekniska färdigheter. Välj vad du vill (och har behov av) för att bli redo. Allt är gjort klart för dig i Readynez365 i god tid för dina utbildningar.
Utbildningsmetodiken är designad till det virtuella klassrummet med fokus på att inspirera och engagera dig med en blandning av praktisk utbildning, presentationer, tekniska labbar och tester. Virtuell utbildning uppskattas också av ledare då det är det mest kostnadseffektiva sättet att utbilda på.
Det finns ett maximalt antal deltagare på utbildningen för att säkerställa enkel tillgång till personlig coaching. Du möter ackrediterade expertinstruktörer som är erfarna IT-proffs och konsulter, certifierade på högsta nivå och som tar med verkligheten in i undervisningen.
Vi täcker alla detaljer så du kan använda det i ditt dagliga arbete och du kommer även lära dig detaljerna du behöver för att klara din examen. Det är ditt beslut om du vill genomföra examen eller inte men med våra detaljerade examensguides och hotline gör vi det enkelt för dig att få tillgång till dina examensvouchers och planera och genomföra din examen online.
Din tillgång till utbildning är obegränsad och du kan utbilda dig så mycket du vill tills du klarar din examen.
Lär dig med gott samvete med utbildningar som ger 96% lägre CO2-utsläpp jämfört med klassrumsutbildning. Vår organisation arbetar med minimal miljöpåverkan och vi har reducerat CO2-utsläppen med 96% sedan 2019. Vi följer ISO 14001 genom hela leveransprocessen som din garanti för hållbar utbildning.
- Grundläggande teori om åtkomstkontroll och lösenordens roll vid hantering av åtkomstkontroll.
- Kritisk aspekt av beredskapsplanering med en affärskontinuitetsplan och katastrofåterställningsplan
- Syfte, implementering och bakgrund av de kritiska säkerhetskontrollerna
- Grundläggande begrepp inom kryptografi
- Högnivåförståelse för de viktigaste typerna av kryptosystem och steganografi.
- Förstå de matematiska begrepp som bidrar till kryptografi
- Identifiera vanliga symmetriska, asymmetriska och hashande kryptosystem.
- Högnivåförståelse för användning, funktionalitet och drift av VPN, GPG och PKI
- Försvar i djupet är och identifiera nyckelområdena för säkerhet
- Demonstrera de olika strategierna för att implementera effektiv säkerhet inom en organisation.
- Hur man skapar ett nätverk som ska övervakas och kontrolleras för att motstå intrång.
- Grundläggande förståelse för funktionen och användningen av endpoint-säkerhetsenheter, såsom endpoint-brandväggar, HIDS och HIPS
- Högnivåförståelse för funktionerna i gruppolicy och arbete med INF-säkerhetsmallar
- Koncept för incidenthantering och processerna kring incidenthantering.
- Hantering av cybersäkerhetsrisk inklusive identifiering av stegen i hotbedömningsprocessen
- En mängd olika Linux-operativsystem, inklusive mobilsystem, för att bättre förstå hur man konfigurerar och säkrar Linux.
- Få insyn i ett Linux-system för att kunna säkra och härda systemet.
- Användning av systembaslinjer, loggfiler och andra verktyg som är gemensamma för Linux-operativsystem för att bättre övervaka system för tecken på attack.
- Hur man använder viktiga säkerhetsverktyg och verktyg som är tillgängliga för Linux-system för att förbättra systemsäkerheten.
- Demonstrera en förståelse på hög nivå för vikten av loggning, inställning och konfiguration av loggning och logganalys med hjälp av SIEM:er
- Förstå viktiga attackmetoder och grundläggande defensiva strategier för att mildra dessa hot.
- Grundläggande förståelse för riskerna med nätverksenheter och hur man säkrar dem.
- Visa en grundläggande förståelse för funktionen och användningen av nätverkssäkerhetsenheter, såsom brandväggar, NIDS och NIPS
- Visa förståelse för egenskaper och funktioner hos nätverksprotokoll och nätverksprotokollstackar.
- Vidta grundläggande åtgärder för att säkra Windows-nätverkstjänster som IPSec, IIS och Remote Desktop Services
- Syftet med och komponenterna i politiken.
- Grundläggande förståelse för riskerna med virtualisering och molntjänster och hur man säkrar dem.
- Koncept och relation bakom spaning, resursskydd, risker, hot och sårbarheter
- Preliminär förmåga att skapa nätverkskartor och utföra penetrationstesttekniker
- Visa förståelse för webbapplikationssäkerhet och vanliga sårbarheter inklusive CGI, cookies, SSL och aktivt innehåll.
- Behörighetsprogram i Windows NT-filsystemet, delade mappar, skrivare, registernycklar och Active Directory, och rättigheter
- Förstå hur man hanterar uppdateringar för ett nätverk av Windows-värdar.
- Tekniker och tekniker som används för att granska Windows-värdar.
- Identifiera skillnaderna mellan typer av Windows-operativsystem och hur Windows hanterar grupper och konton, lokalt och med Active Directory och gruppolicy
- Grundläggande förståelse för missuppfattningar och risker med trådlösa nätverk och hur man säkrar dem.
Möt några av de instruktörer du möter på din kurs. De är experter, passionerade inom sina områden och dedikerade till att hjälpa de som vill lära sig, utforska och bli framgångsrika i sina karriärer.

Kevin Henry är en globalt erkänd expert som i över 20 år har bidragit till att utbilda och certifiera människor inom IT-säkerhet, inklusive CISSP, CISM, CISA och andra.

James Rowney är en välkänd expert med över 20 års bidrag till utbildning av IT-säkerhetsfärdigheter.

Friedhelm har mer än 30 års erfarenhet inom IT, säkerhet och datasekretess som senior informationssäkerhetskonsult.
På Readynez tillhandahåller vi många resurser och har erfarna experter på området. Det är därför vi också är mycket framgångsrika med många nöjda kunder. Du kan därför tryggt gå din kurs hos oss. För att gå GSEC-kursen krävs dock några förkunskaper.
Du har den perfekta utgångspunkten för att ta den här kursen med dessa förkunskaper:
Med 15 års erfarenhet och fler än 50.000 nöjda kunder från hela världen litar organisationer som ALSO, ATEA, Microsoft, Serco och många fler på Readynez att utbilda och certifiera deras medarbetare.
![[Dictionary item: Green-check]](/images/green-check.png) Toppbetyg på kurser där flest deltagare ger kursen 10/10
Toppbetyg på kurser där flest deltagare ger kursen 10/10![[Dictionary item: Green-check]](/images/green-check.png) 50.000 deltagare utbildade och certifierade
50.000 deltagare utbildade och certifierade![[Dictionary item: Green-check]](/images/green-check.png) Globalt erkända expertinstruktörer, flertalet MVP
Globalt erkända expertinstruktörer, flertalet MVP![[Dictionary item: Green-check]](/images/green-check.png) Pålitlig leverantör av stora utbildningsprojekt för många stora organisationer
Pålitlig leverantör av stora utbildningsprojekt för många stora organisationerDetta är bara några av de många organisationer som litar på Readynez




Utvida din expertis inom skysäkerhet med det certifierade kursen i Cloud Security Essentials (GCLD). Ledet af brancheeksperter leverer detta program omfattande träning til at styrke cloudmiljøer. Få praktiska färdigheter för att skydda data och applikationer i skyen. Bliv på forkant inden för det utvecklande kändes av cybersäkerhet med praktisk inlärning, och optjen den efterspurgte GCLD-certifiering för att validere dine cloud-säkerhetsfærdigheder.
SE KURSFrigör detta potentiella inden för etisk hacking med det certifierade kurset i Penetration Tester (GPEN). Ledet af brancheeksperter leverer detta program praktisk träning for at mestre kunsten at gennemtrænge test. Få avancerade färdigheter att identifiera och adressera sårbara och säkra robusta cybersäkerhetsforsvar. Löft din expertis och validerar dina färdigheter med den efterspurgte GPEN-certifieringen och positionerar dig som en cybersäkerhetsprofessionel.
SE KURSThe Virtual Classroom is an online room, where you will join your instructor and fellow classmates in real time. Everything happens live and you can interact freely, discuss, ask questions, and watch your instructor present on a whiteboard, discuss the courseware and slides, work with labs, and review.
Yes, you can sit exams from all the major Vendors like Microsoft, Cisco etc from the comfort of your home or office.
With Readynez you do any course form the comfort of your home or office. Readynez provides support and best practices for your at-home classroom and you can enjoy learning with minimal impact on your day-to-day life. Plus you'll save the cost and the environmental burden of travelling.
Well, learning is limitless, when you are motivated, but you need the right path to achieve what you want. Readynez consultants have many years of experience customizing learner paths and we can design one for you too. We are always available with help and guidance, and you can reach us on the chat or write us at info@readynez.com.
Datum:
Tider: