Få nye IT kompetencer, bliv certificeret og løft din IT-karriere til nye højder uden at sprænge banken!
Unlimited Training - IT Kurser og Certificeringer gjort helt enkelt og utroligt billigt. Få adgang til 60+ Top LIVE kurser for mindre end prisen for ét kursus.











course: ISC2 HCISPP - HealthCare Information Security and Privacy Practitioner
Varighed: 3 days
Format: Virtual or Classroom
![]() Forbereder til Eksamen :
ISC2 HealthCare Information Security and Privacy Practitioner (HCISPP)
Forbereder til Eksamen :
ISC2 HealthCare Information Security and Privacy Practitioner (HCISPP)
![]() Forbereder til Certificering :
ISC2 Healthcare Information Security & Privacy Practitioner (HCISPP)
Forbereder til Certificering :
ISC2 Healthcare Information Security & Privacy Practitioner (HCISPP)
At opnå ISC2 HCISPP - HealthCare Information Security and Privacy Practitioner certificeringen er ikke en nem opgave, men med dit Readynez kursus og Learning Program har vi gjort alt, hvad vi kan for at støtte dig fra start til slut, og sikre at du har de optimale betingelser for at få succes. Det inkluderer de bedste tilgængelige ressourcer til at hjælpe dig med at forberede dig, herunder relevante online kurser, adgang til praktiske labs, Practice Tests til eksamensforberedelse, study guides, eksamenssupport og guider osv., alt sammen gjort let tilgængeligt for dig i vores Learning Platform. Vælger du vores virtuelle træningsmulighed, bidrager du også til en mere bæredygtig verden med en reduktion i CO2-udledning på 96% sammenlignet med muligheden i klasseværelset.
![[Dictionary item: Green-check]](/images/green-check.png) Inkluderer omfattende læringsmaterialer for den bedst tænkelige eksamensforberedelse
Inkluderer omfattende læringsmaterialer for den bedst tænkelige eksamensforberedelse![[Dictionary item: Green-check]](/images/green-check.png) Ingen forældede og forudindspillede videoer. Opdaterede og Live instruktørledede sessioner - garanteret!
Ingen forældede og forudindspillede videoer. Opdaterede og Live instruktørledede sessioner - garanteret!![[Dictionary item: Green-check]](/images/green-check.png) Inkluderet i vores Unlimited Training tilbud, som giver dig Unlimited adgang til sikkerhedskurser
Inkluderet i vores Unlimited Training tilbud, som giver dig Unlimited adgang til sikkerhedskurser![[Dictionary item: Green-check]](/images/green-check.png) Fuld support tilgængelig, der hjælper dig med at tilmelde dig, forberede dig til og gennemføre din eksamen
Fuld support tilgængelig, der hjælper dig med at tilmelde dig, forberede dig til og gennemføre din eksamenISC2 HCISPP - HealthCare Information Security and Privacy Practitioner-uddannelseskurset er designet til fagfolk i sundhedssektoren, der er ansvarlige for at sikre og vedligeholde privatlivets fred for sundhedsoplysninger. Det dækker emner som sundhedsbestemmelser, privatlivs- og sikkerhedsprincipper, risikostyring, informationsstyring, tredjeparts risikostyring og udvikling af sikkerhedsprogrammer. Ved at gennemføre kurset og opnå HCISPP-certificeringen demonstrerer fagfolk deres ekspertise inden for sundhedsinformationssikkerhed og privatliv. Certificeringen validerer deres evne til at navigere i de unikke udfordringer og regulatoriske krav i sundhedssektoren, implementere effektive sikkerhedskontroller og håndtere informationsrisici. Det udstyrer dem med de nødvendige færdigheder til at beskytte sundhedsdata og bidrage til udviklingen af robuste sikkerheds- og privatlivsprogrammer i sundhedsorganisationer.

Readynez er den bedste træningsudbyder, jeg har brugt i mange år. Deres kundeservice er førsteklasses, priserne er meget konkurrencedygtige og instruktørerne er fremragende.

Nemt at deltage på kurset over Teams og en fremragende instruktør gav mig stor værdi for den tid, jeg investerede.
Dit personlige Learning Program vil give dig de kompetencer du har brug for, så du kan gøre mere af det du elsker. Learning Programmet's tre step er lavet, så du lærer nye kompetencer der vil åbne nye muligheder for dig.
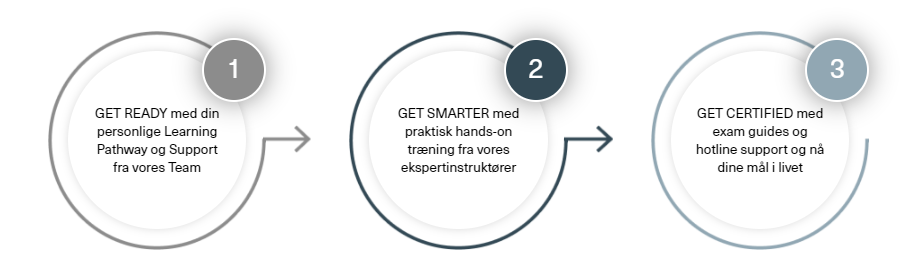
Readynez365 platformen giver en forbedret digital vej for alle dine læringselementer, fra forberedelser til eksamen, hvilket gør det til den mest direkte vej til nye tekniske færdigheder. Vælg hvad du vil (og har brug for) for at blive klar. Det hele er gjort klar til dig i Readynez365 i god tid før dine kurser.
Træningsmetodikken er designet til det virtuelle klasselokale, med fokus på at inspirere og engagere dig med en blanding af praktisk træning, præsentationer, tekniske labs og tests. Du vil også være glad for at vide, at virtuel træning er elsket af ledere - det er nemlig den mest omkostningseffektive måde at træne på.
Der er et maksimalt antal deltagere på holdet for at sikre dig nem adgang til personlig coaching. Du vil møde akkrediterede ekspertinstruktører, der er erfarne IT-professionelle og konsulenter, der er certificeret til det højeste niveau, og som bringer den virkelige verden ind i undervisningen.
Vi dækker alle detaljerne så du kan anvende det i dit daglige arbejde, og du vil endda lære de detaljer, du skal kende til ifm din eksamen. Det er dit valg, om du vil gå til eksamen eller ej, men med vores detaljerede eksamensguides og hotline gør vi det nemt at få adgang til din eksamensvoucher og planlægge og gennemføre din eksamen online
Din adgang til træning er ubegrænset, og du kan træne lige så meget, du vil, indtil du består din eksamen.
Træn med god samvittighed med kurser der giver et 96% lavere CO2-aftryk sammenlignet med træning i klasselokalet. Vores organisation opererer med minimal miljøpåvirkning, og vi har reduceret vores CO2-udledning med 96% siden 2019. Vi overholder ISO 14001 gennem hele vores forsyningskæde som din garanti for vores bæredygtige kurser.
- Typer af organisationer i sundhedssektoren (f.eks. udbydere, lægemidler, betalere)
- Sygesikring (f.eks. skadebehandling, betalingsmodeller, sundhedsbørser, clearingcentre)
- Kodning (f.eks. Systematized Nomenclature of Medicine Clinical Terms (SNOMED CT),
- Indtægtscyklus (dvs. fakturering, betaling, refusion)
- Workflow Management
- Reguleringsmiljø
- Folkesundhedsrapportering
- Klinisk forskning (f.eks. processer)
- Administration af sundhedsjournaler
- Sælgere
- Forretningspartnere
- Regulatorer
- Andre Tredjepartsforhold
- Informationsflow og livscyklus i sundhedsmiljøerne
- Karakterisering af sundhedsdata (f.eks. klassificering, taksonomi, analyser)
- Datainteroperabilitet og -udveksling (f.eks. Health Level 7 (HL7), International Health Exchange (IHE), Digital
- Billedbehandling og kommunikation i medicin (DICOM))
- Juridiske lægejournaler
- Sikkerhedsstyring (f.eks. chartre, roller, ansvarsområder)
- Privatlivsstyring (f.eks. chartre, roller, ansvarsområder)
- Politikker
- Standarder
- Processer og procedurer
- Organisatorisk etisk kodeks
- (ISC)² Etisk kodeks
- Øget eksponering, der påvirker fortrolighed, integritet og tilgængelighed (f.eks. trusselslandskab)
- Tilsyn og regulatoriske udfordringer
- Interoperabilitet
- Informationsteknologier
- Tillidsmodeller for tredjepartsforbindelser
- Tekniske standarder (f.eks. fysisk, logisk, netværksforbindelse)
- Tilslutningsaftaler (f.eks. Memorandum of Understanding (MOU), Interconnection Security Agreements (ISA'er))
- Juridiske spørgsmål, der vedrører informationssikkerhed og privatliv for sundhedsorganisationer
- Dataovertrædelsesbestemmelser
- Beskyttede personlige oplysninger og helbredsoplysninger (f.eks. personligt identificerbare oplysninger (PII), personlige helbredsoplysninger (PHI))
- Jurisdiktionsimplikationer
- Registrerede
- Forskning
- Traktater
- Love og forordninger (f.eks. EU's (EU) databeskyttelsesdirektiv, lov om overførsel og ansvarlighed for sundhedsforsikringer/sundhedsinformationsteknologi for økonomisk og klinisk sundhed (HIPAA/HITECH), General Data Protection Regulation (GDPR), beskyttelse af personlige oplysninger og elektronisk Documents Act (PIPEDA))
- Privacy Frameworks (f.eks. Organisationen for Økonomisk Samarbejde og Udvikling (OECD) Privatlivsprincipper, Asia-Pacific Economic Cooperation (APEC), Generally Accepted Privacy Principles (GAPP))
- Sikkerhedsrammer (f.eks. International Organization for Standardization (ISO), National Institute of Standards and Technology (NIST), Common Criteria (CC))
- Fortrolighed
- Integritet
- Tilgængelighed
- Identitets- og adgangsstyring (IAM)
- Datakryptering
- Træning og opmærksomhed
- Logning, overvågning og revision
- Sårbarhedshåndtering
- Funktionsadskillelse
- Mindst privilegium (nødvendigt at vide)
- Business Continuity (BC)
- Disaster Recovery (DR)
- Systemsikkerhedskopiering og -gendannelse
- Samtykke/valg
- Begrænset indsamling/lovlig formål/formålsspecifikation
- Oplysningsbegrænsning/Overførsel til tredjeparter/Grænseoverskridende bekymringer
- Adgangsbegrænsning
- Nøjagtighed, fuldstændighed og kvalitet
- Ledelse, Udpegning af Privacy Officer, Supervisor Re-autorisation, Behandlingsautorisation og ansvarlighed
- Træning og opmærksomhed
- Gennemsigtighed og åbenhed (f.eks. meddelelse om privatlivspraksis)
- Proportionalitet, brug og offentliggørelse og brugsbegrænsning
- Adgang og individuel deltagelse
- Meddelelse og formålsspecifikation
- Hændelser, hændelser og brud
- Afhængighed
- Integration
- Reduktion af følsomhed (f.eks. afidentifikation, anonymisering)
- Kategorier af følsomme data (f.eks. adfærdsmæssig sundhed)
- Identifikation af informationsaktiver
- Værdiansættelse af aktiver
- Eksponering
- Sandsynlighed
- Indvirkning
- Trusler
- Sårbarhed
- Risiko
- Kontrolelementer
- Restrisiko
- Accept
- Definition
- Fremgangsmåde (f.eks. kvalitativ, kvantitativ)
- Hensigt
- Livscyklus/kontinuerlig overvågning
- Værktøjer/Ressourcer/Teknikker
- Ønskede resultater
- Rolle som intern og ekstern revision/vurdering
- Informationsindsamling
- Estimeret tidslinje for risikovurdering
- Gap-analyse
- Afbødende handlinger
- Undgåelse
- Overførsel
- Accept
- Kommunikation og rapportering
- Administrativ
- Fysisk
- Teknisk
- Tredjepartsrolle/relation til organisationen
- Brug af sundhedsoplysninger (f.eks. behandling, opbevaring, transmission)
- Relationsledelse
- Organisatoriske standarder
- Udløser af en tredjepartsvurdering
- Kontroller til beskyttelse af informationsaktiver
- Overholdelse af kontrolelementer til beskyttelse af informationsaktiver
- Kommunikation af resultater
- Risikostyringsaktiviteter
- Identifikation af risikobehandling
- Korrigerende handlingsplaner
- Dokumentation af overholdelsesaktiviteter
- Interne processer for Incident Response
- Forholdet mellem organisation og tredjemands hændelsesreaktion
- Genkendelse af brud, meddelelse og indledende reaktion
- Organisatorisk overtrædelse af notifikationsregler
- Organisatoriske politikker og standarder for formidling af information
- Risikovurderingsaktiviteter
- Chain of Custody Principper
- Kortlægning af informationsflow og omfang
- Datafølsomhed og klassificering »Privatlivs- og sikkerhedskrav
- Risici forbundet med tredjeparter
Mød nogle af de instruktører du kan møde på dit kursus. De er eksperter, passionerede omkring deres fag og dedikerede til at give deres viden tilbage til branchen, deres fag og dem som ønsker at lære, udforske og skabe fremskridt i deres karriere.

Kevin Henry er en globalt anerkendt ekspert som i over 20 år har bidraget til at træne og certificere folk indenfor IT Sikkerhed, inklusive CISSP, CISM, CISA m.fl.

James Rowney er anerkendt for sine mere end 20 års bidrag til træning og certificering indenfor IT Sikkerhed.

Friedhelm har mere end 30 års erfaring indenfor IT, Sikkerhed og Data Privacy som en Senior Information Security konsulent.
Hos Readynez stiller vi mange ressourcer til rådighed og har erfarne eksperter på området. Derfor har vi også stor succes med mange tilfredse kunder. Du kan derfor trygt tage dit kursus hos os. For at tage HCISSP-kurset kræves der dog nogle forudsætninger.
Du har det perfekte udgangspunkt for at tage dette kursus med disse forudsætninger:
Med 15 års erfaring og mere end 50.000 glade kunder fra hele verden, organisatiner som ALSO, ATEA, Microsoft, Serco og mange flere, stoler på Readynez til at træne og certificere deres medarbejdere.
![[Dictionary item: Green-check]](/images/green-check.png) Top bedømte kurser, med flest deltagere som scorer deres kursus 10/10
Top bedømte kurser, med flest deltagere som scorer deres kursus 10/10![[Dictionary item: Green-check]](/images/green-check.png) 50.000 deltagere trænet og certificeret
50.000 deltagere trænet og certificeret![[Dictionary item: Green-check]](/images/green-check.png) Globalt anderkendte ekspert instruktører, mange som er MVP
Globalt anderkendte ekspert instruktører, mange som er MVP![[Dictionary item: Green-check]](/images/green-check.png) Betroet leverandør af store træningsprojekter for mange store organisationer
Betroet leverandør af store træningsprojekter for mange store organisationerDette er bare nogle af de mange organisationer som stoler på Readynez.




På dette Readynez-kursus lærer du, hvordan du begrænser en hændelse, beskytter aktiver og behersker de komponenter og procedurer, der er nødvendige for en omfattende responsplan (IRP).
SE KURSUSThe goal of this five-day immersed SSCP course is to provide IT and information security professionals with a fully-immersed, zero-distraction, all-inclusive SSCP training experience.
SE KURSUSThe Virtual Classroom is an online room, where you will join your instructor and fellow classmates in real time. Everything happens live and you can interact freely, discuss, ask questions, and watch your instructor present on a whiteboard, discuss the courseware and slides, work with labs, and review.
Yes, you can sit exams from all the major Vendors like Microsoft, Cisco etc from the comfort of your home or office.
With Readynez you do any course form the comfort of your home or office. Readynez provides support and best practices for your at-home classroom and you can enjoy learning with minimal impact on your day-to-day life. Plus you'll save the cost and the environmental burden of travelling.
Well, learning is limitless, when you are motivated, but you need the right path to achieve what you want. Readynez consultants have many years of experience customizing learner paths and we can design one for you too. We are always available with help and guidance, and you can reach us on the chat or write us at info@readynez.com.
Datoer:
Tider: